
Today’s threat actors and social engineers leverage social media to observe individuals’ patterns and habits. They encounter you at a coffee shop or another familiar spot. They begin to establish trust, which makes you more susceptible to their tactics.
Today’s guest is Peter Warmka. Peter is a retired CIA officer with over two decades of breaching the security of organizations overseas in pursuit of intelligence. He is the founder of The Counterintelligence Institute, author of two books, conference speaker, consultant, and educator on the dangers of human hacking.
“Human hacking is hacking into someone’s mind and getting to know how their mind works with the goal of manipulation.” - Peter Warmka Share on XShow Notes:

- [0:56] – Peter shares his background and what he has done in his interesting career.
- [3:27] – The Counterintelligence Institute helps organizations and individuals understand what types of information threat actors are trying to steal.
- [6:08] – Peter discusses the surprise his friends and family experienced when learning he had been working for the CIA.
- [9:13] – There are some skills that Peter had to learn when going into this career, but other skills came more naturally.
- [11:15] – Trust is different in various societies, and Americans are particularly vulnerable.
- [13:31] – Peter explains how he developed trust with others.
- [16:00] – There are ways to leverage trust in this type of work.
- [19:32] – Peter discusses international breaches and the types of intelligence breaches from other governments.
- [23:11] – The internet has made information so readily available to everyone, including information you may not want them to have.
- [25:19] – There are different types of information found on the different kinds of social media platforms that all come together to paint a whole picture.
- [28:09] – Human hacking, or social engineering, can be accomplished through five different communication channels.
- [31:21] – Peter describes a very powerful and common in-person scenario.
- [35:53] – We have to get away from the silo-approach, thinking that breaches are only coming from the IT network.
- [37:24] – Peter wrote a book in the early days of Covid-19 for organizations. He then wrote a book geared more towards individuals.
- [39:41] – Privacy and security settings are great, but platforms can still be hacked.
- [41:56] – It shouldn’t be “trust, then verify.” It needs to be “verify, then trust.”
- [44:27] – AI tools have made things even more complicated for victims and easy for threat actors.
- [46:37] – LinkedIn specifically is overwhelmed with fake accounts.
- [48:50] – Workplace education on this topic is backwards in organizations since they are seen as compliance training.
Thanks for joining us on Easy Prey. Be sure to subscribe to our podcast on iTunes and leave a nice review.
Links and Resources:
- Podcast Web Page
- Facebook Page
- whatismyipaddress.com
- Easy Prey on Instagram
- Easy Prey on Twitter
- Easy Prey on LinkedIn
- Easy Prey on YouTube
- Easy Prey on Pinterest
- Counterintelligence Institute Website
- Peter Warmka on LinkedIn
Transcript:
Peter, thank you so much for coming on the Easy Prey Podcast today.
Thank you, Chris. I appreciate the opportunity. It's great.
I'm looking forward to this. Can you give my audience a little bit of background about who you are and what you do?
I spent a 23-year career with the Central Intelligence Agency. Most of that time, 20 years were spent directly overseas, working in a variety of countries based in a number of countries, and also traveling to a number of other countries.

I think before we started the show, we were talking a little bit about how I got in and everything, but there was a little bit of an anecdote that's kind of funny because I worked most of my career deep undercover. It wasn't like people knew, even my family knew who I was working for, only my wife, when I initially was recruited. My three children didn't know until they were about 17 or 18 years old.
Before I went to my first overseas post, the CIA said, “We want you to inform one of your family members stateside. In case there's ever an emergency, we can contact them and they know this is not some kind of scam.” I decided to tell my father, a very patriotic man, and I thought he was going to be very proud of me. He's a farmer in central Wisconsin, and I went up for a weekend. I said, “Dad, I need to talk to you about kind of who I'm working for and why I'm going overseas.” He listened attentively. Then when I finished, he looked me in the eyes and he said, “Son, I wish you wouldn't have told me. Don't tell your mother.”
I was kind of really shocked. It wasn't because he was against it. He was, just like a lot of people, don't really understand what the CIA does. He was thinking about the things that he hears about or sees in movies, and that is very dangerous.
I said, “Dad, don't worry. Everything's going to be fine,” and so he kept that secret until about two years before he passed. He passed away when he was 96. Then he began to tell my siblings. My sibling said, “Peter’s working for the CIA. Dad is losing it. What is going on? Can you imagine Peter working for the CIA?”
I think maybe he knew his time was getting shorter and he wanted to make sure someone else knew. I don't know. But in any case, it wasn't until I almost retired that I decided to come out into the light, and I was able to share the fact that I worked for the agency and try to use some of those skills that I learned for helping organizations today.
I set up my own consultancy firm Counterintelligence Institute. We focus on how to help organizations understand what are the threats out there. Who are the threat actors? What type of information are they trying to steal when they try to breach the organization? It's not always through the IT network. There are a lot of other ways that organizations can be breached to take the most likely information.
What type of information are they trying to steal when they try to breach the organization? It's not always through the IT network. There are a lot of other ways that organizations can be breached to take the most likely… Share on XThen, also working with individuals, because it's not only companies themselves, but it's usually the individuals. That's the gateway into a breach into a company, and there are also individuals who are very vulnerable in their own right and stand to lose a lot of money due to a variety of different frauds and scammers that use a lot of the same methodology that we're going to talk about.
I'm always curious about people who've worked, who work in this vertical. Was it hard to maintain this kind of dual life of, “Here's what I'm really doing, but here's what I have to tell people I'm doing”?
At first, I thought it was going to be really difficult because I grew up in a you don't lie, even white lies. White lies, maybe, but you tend to be very honest, and it's also, I think, very difficult for my father because people would ask my father, “What Peter is doing?” He felt really bad about not being able to tell the truth. For myself, I think I gradually just came accustomed to it, and you have that dual…it is really weird. You're able to segregate what is the real part of your life with what is fictional part of your life.
I guess for me, it just became important to know, “I'm doing this. I'm lying. I'm doing the work I'm doing for the greater good.” At least in my eyes, it's for the greater good of trying to help my nation, help my country. That was the ultimate goal. I felt that it was justified, to put it that way.
Yeah. I had interviewed John McAfee before he passed away, and one of the things that he said was the hardest thing for him was having—he was also on the run, so a little different situation—but he just felt bad about how having to lie and consistently lie to friends and family, and that was something that he hadn't expected as being one of the challenges of that.

I mean, you don't know what’s going to be the result later when they do find out and, fortunately in my case, when I told my children, they were surprised, of course, but they thought it was pretty cool. When I told my siblings, they all said, “Now things make sense. This is kind of weird. We didn't know how you were moving from country to country and doing different types of things, and your resume looked awful, but then it started to make sense.”
Even a number of the individuals who I recruited as sources and with whom I maintain contact, at least had more contact within these last few years found out, of course, who I was with, the organization I was working for, when I recruited them and didn't realize it until afterward. I think they were very shocked and so they probably went through a mix of emotions of, “You lied to me” or whatever, but they realized that we had a true friendship and we still do.
Most people will understand. Some kids of agency officers might take it the wrong way, might not accept it, might be upset, and might feel like you lied to them all these years. I think if anybody would like to see what that kind of life is, look at The Americans, the series, at least the part where the children find out what their parents were doing, who they were really working for. It can be a real eye-opener for children.
Were you out of the CIA when you told them that you worked for the CIA, or were you still there?
I was still there, but it was getting to the point where my eldest were, I think, 16 and 14. We usually would come back to the States for physicals and other things, but not in the Washington area. They wanted us to come back to the Washington area. They even wanted to have a psychologist, just a routine visit with the kids.
I'm thinking, my kids, they're going to say, “This is really strange.” I had my wife stay with the youngest one in another hotel room. She was just too little, and I told the older two and said, “I want to tell you who I really work for.” My daughter was going, “Yeah, dad; stop joking.” My son was quiet, but his eyes kept on getting wider and wider. Then finally he said, “It all makes sense to me now because my friends would say he's always traveling and doesn't seem to have colleagues at work. Maybe he's a drug addict, he's a money launderer, a drug dealer.” My son was thinking, “I don't think so.”
My daughter just thought I was joking and finally they both realized this is so cool. My youngest daughter, I told probably two years before I left. I was in the DC area and they had a family day at Langley. I said, “Hey, you want to find out where I work?” And she thought I was going to take her to the State Department. She thought this was going to be boring.
When we walked, we drove onto Langley and she saw this, you work here and we went. We went directly to the seventh floor of the new building. That's where the director was and I took her in to see the director, and that was Director Hayden. I said, “This is my daughter. She just found out who I work for today.” He grabbed your hand in a handshake like this. He said, “Young lady, welcome to our family.” It was so cool. It was so neat.
I love hearing about stories of this stuff. You definitely had a skillset that you had to cultivate in order to—I don't want to say manipulate people—interact with people, and get them to do things that you wanted them to do. What were some of the skills that you had to learn?
I think some skills were natural and other ones were learned. One of the big skill sets is the arts of elicitation, which some people naturally have. Other people can learn and develop that. I think for me it was a combination.
You're able to have a conversation with somebody, and it appears to be just a casual conversation. Maybe you meet somebody at a bar, maybe you're meeting them, and you're sitting next to them on the airplane, or you're at the fitness center, and you just strike up what appears to be a random conversation. You move that conversation around because you have certain objectives and it could be twofold.
You might want to get some information, learn some information that this person has access to in their company. You might want to learn some sensitive information regarding this individual's company, or you might want to learn about this individual as a potential target for recruitment because of the work that that person does, the organization that they are affiliated with, and the access to intelligence information that we might want to collect.
There’s a lot of different techniques within elicitation, but typically about 11, and we just move the conversation around to try to get at specific bits and pieces of information, and it's important for us to ask that question, or we make a comment and we try to get that individual to also comment on something, and then we just shut up.
We listen and we collect that information and we move it around and, um, maybe we'll try to get follow-up conversations with this person. We try to get a hook into them. We try to develop a social relationship with them because we might have a pretext. Maybe we have a pretext for why we actually call them up to get together for X, Y, and Z could be for business. It could be for something else. Then we want to get the hook into them so we can have repetitive meetings with them and so we're using this elicitation.
We're gaining trust with them. It's very important. This is one of the key things is building that trust because the more trust they place in us, and I found so many cases that they'll count us within their close circle of friends because, in a lot of societies, there's differences in how trust is OK to say the conceived.

Here in America, everybody seems to trust everybody, and we can talk more about that later, but that's a vulnerability. In other countries, there are circles of trust. You may trust your really close family members, maybe out to your cousins and aunts and uncles. Then the people you went to school with since kindergarten—that’s your circle of trust.
People outside that circle, you don't automatically trust them. In fact, in some places, that's fair game to take advantage of those people because it's outside of your tribe, let's say. For me, gaining that trust to the point when I decided that it was an appropriate time to make a recruitment pitch with the individuals that I had, I knew that they were going to accept the agreement to undertake what I was going to ask of them.
One of those key things was that they fully trusted me. They fully trusted what I was telling them. They fully trusted that I would do everything I could to protect them and our relationship. I never had anyone turn me down, put it this way.
It's kind of amazing. I'm not bragging, but I think it's because of that relationship. We could look at a relationship of maybe six months to maybe a year or more, depending upon maybe the cultural norms of the individual that you're dealing with, because in some societies it's a much longer period of cultivation.
As I say, it's like a lawyer. Lawyers never ask questions that they don't know the answer to.
Exactly. There's always a few curveballs that could come into place, but you pretty much know. You pretty much know that this person is going to accept. You might even do a few little minor tests along the way asking for information that may be quite sensitive and find out that they provided it could be bad for them in a sense of losing their job or something worse. You do this test along the way and you feel pretty confident that they're going to accept.
What are some of the kinds of conceptual questions that you would ask to test the level of trust that the person has in you?
First of all, what I like to develop in a relationship and really get to know an individual is that maybe the first place that I meet them is going to be in their office. I can learn a lot about them in their office, look at what their office looks like, the awards, the degrees they have on the walls, artwork, and pictures from their children. You can learn a lot from that and how they engage with other coworkers.
They don't like to meet with them in their house. See, if they're married, maybe meet their spouse, a partner, get to see their children, kind of like learn a little more about their socioeconomic status. Then almost all that remaining time is one-on-one with them away from the office, away from work, where they can tell me a lot of things that they can't confide to anybody at the workplace. They can't really confide in their spouse, but I can become one of their best friends.
Little by little, I try to learn as much as possible. I need to confirm that they have access to the information that I believe they have so I started asking them questions, sensitive questions, and maybe even asking them to bring me something, maybe a document or something.
Little by little, while they do that to please me and to also show that, “Yeah, I got this.” I want to be able to say, “I need this for XYZ. This can also help me. Maybe I'm sharing this with somebody, but don't worry; this is very, very closely held, and no one's going to find out that you gave it to me.”
Some of these little tests along the way, you see that they're cooperating with you and you can turn this now into something even bigger. I've learned that maybe you have some financial challenges up ahead. You want to send your kids to good universities, or you want to be able to move up in your career and there are some things that I can do for you or help you with that help you move up in your career. There are a lot of different motivations or needs that people have and so it's not only the motivations; there's also vulnerabilities.
There are a lot of different vulnerabilities. The number one is going to be financial. Again, it's not having lots of money. It's going to be a financial duress, not knowing how you're going to pay next month's mortgage or next month's rent. That can be gut-wrenching. That causes a lot of problems. A couple separate or divorce and people begin to drink and take drugs. That's a big one and a vulnerability that we can leverage.
Let's say we want to help; it's got to be a win-win typically. It's not like other intelligence services that will blackmail the worst people, because the Russians will do this and a number of other ones. I'll be honest with you. I can't say it never ever happened in the CIA, but I've never seen it happen, and it's never been part of my operations. It's always a win-win. We want to ensure that that person's getting the need that's being met and they're providing us with information that's meeting our needs.
But a few of these other vulnerabilities that are interesting are revenge. There are people that despise a place where they work, to despise their supervisor, to despise the owner of the company. They're there because they need a salary. But if you give them an opportunity to get back at their employer, they'll likely take that. Or there are people that have strong egos.
If you say, “I don't think nobody could do that. You wouldn't be able to accomplish that.” They said, “Yes, I can. Of course, I can and I'll show you.” I mean, it's like the only way to push buttons. There are a lot of people that can get involved, especially the term asset—people that work for us—and ego sometimes is part of this.
Psychology is a very, very important tool or element here within the world of espionage when we talk about dealing with people recruiting people. It's a core discipline that we need to learn and nurture along the way, and so that's why I think it's also how we can use these types of things today and understanding whether we're individuals or whether we're companies, we want to protect ourselves. What are the ways that different threat actors can go after you using some of the same methodology.
I'm no longer in that game of espionage, but being able to try to educate people that this stuff is out there and anybody can be targeted. You don't have to be in some position of having access to classified information to be a target. No, not at all. There’s a lot of other common people that can easily be targeted.
Do you see that happening a lot in the US of people being not necessarily targeted by agencies, but by individuals or companies that just want to know more about their competitors? Is that kind of something that happens?
Oh, absolutely. I say threat actors, a lot of times people think criminals. If you look at that organization, that pie chart, where are the threats coming from? Criminals are like a good 80%. Yes and no. I mean, it's true that the majority of them come from criminal groups, but we don't even know, really, because a lot of these criminal groups are also working in tandem with intelligence services.
There are intelligence services that will use criminal groups to conduct operations and try to hide the attribution of the intelligence service. Some of these criminal groups actually have individuals who were former intelligence officers for the KGB and other and the Chinese and other services.
A lot of it is gray. It's not black and white. There's criminal groups, of course, but the largest intelligence services are huge, and we can look at pretty much anyone's services, but let me just take two quick ones.
You think of ransomware, people think it's criminal groups. By far, criminal groups are heavily involved in that, but the number one group involved in ransomware is the North Korean intelligence services. The number one.
The Chinese are very active in espionage and targeting individuals. There were four major breaches. Some of your listeners probably are aware of them. Others not. I mean, they've been acknowledged by the US government as being conducted by the Chinese intelligence services. These are the OPM, the Marriott, and the Equifax.

These happened all between the years 2014 to 2015. Why do we think that, “Well this was not a criminal group”? First of all, when a criminal group typically breaches an organization, they were going to put up that information. They're going to sell it. It might be on the dark web. But with these particular four breaches, these were not disclosed in the dark web. It means that information is being held for some other reason. It was the United States government that confirmed that it was the Chinese, and I'll just think about this.
Think about the OPM, the Office of Personnel Management. It basically is the clearing house or the repository of information that's collected when background investigations are conducted prior to issuing a clearance to a US citizen to give them access to classified information.
There were almost 22 million individuals who had clearances that had their information sucked up by the Chinese during this breach. It's amazing the amount of information. I mean, everything you can imagine, information that even your spouse does not know about. I mean, the good, the bad and ugly; everything that's there to include, even some biometrics, fingerprints.
I was part of this breach. My wife and I know a lot of other people and all we got was basically, “Sorry. We're going to provide you with credit monitoring or identity theft protection for a year, thank you very much, for free.” That's to think about all that information that's being held.
Then we had the Equifax breach—about 150 million Americans. Think about all your credit information. Then think about Anthem, which was like 78 million, and it's a healthcare provider. All that information. Then Marriott will include all the information of these hotels, international hotels, collected on you when you're traveling, especially if you're part of their rewards program, to include your passport.
Why would the Chinese want this? In my opinion, no one really talks about this very much, they want this information to be used when they want to target individuals who would be of interest to them as potential intelligence sources or individuals who they could recruit and manipulate into becoming agents of influence against the US government.
It's a huge area, and a lot of people aren't aware of it, and I'm sure the Chinese are continuing to look for ways to collect information on people. That's a big swath. If you look at Equifax, you're already looking at maybe almost half the US population.
We got criminal groups, we got intelligence services, we got industrial competitors that will also collect information to try on their competitors. You have activist groups that will also try to collect information so that they can try to damage the reputation of companies.
What all of these have in common and the methodology they're using is they're first of all going to collect as much information as they can open source. Open source means things that you can find on the web, on the internet.

Before the internet, we went to the library, but now there's so much information available and so you could have somebody in Beijing in a Starbucks with a laptop and targeting you, targeting the organization that you work for, and it's so much information that can be collected.
But one of the most important areas is going to be identifying potential insiders in your company. They can target people whether they're employees or contractors. People that have regular unescorted access into the facility or access onto the IT networks.
The day when I was on the field, this was not so easy. We got maybe an organizational chart, maybe they had pictures, maybe they didn't, maybe they would have a name and maybe a title. We had to imagine who was who, what was their responsibility?
Now, number one, go to places for everybody, including intelligence services, criminal groups, and the LinkedIn platform is huge. There's over a billion profiles on LinkedIn, and we can easily do a search and find right away. We can develop a list of preferred candidates based on LinkedIn.
Then we can use a lot of other social media platforms to collect that assessment information, that motivation, those vulnerabilities that I talked to you about. Developing that release, that one-on-one relationship, took time. But using the Internet and social media, a lot of that information now can be just collected over the internet without even exposing yourself as the threat actor. We can step behind that terminal and we can collect this information and then we can use that information for actually targeting individuals.
Now think about what LinkedIn can provide you with your academic and professional work background. Maybe some of the insight into your career progression and where you want to go, your influencers, your volunteer work. What are your passions outside of the workplace? Go to Facebook. A lot of your listeners are on Facebook, hobbies, interests, your favorite sports teams, your favorite concerts, your favorite books. Where have you traveled to? Who did you travel with? Where are you planning to travel in the future? Pictures are worth a thousand words.
We can learn about your social economic status. We can learn about your family, your close contacts, and friends. Then you go onto Twitter, X. That can get into your head. What are you thinking about? What are things that motivate you? What are your ideology, religious convictions? What are your pet peeves?
Then they can move on to Instagram. Think about all these people that when they go out to a restaurant, the waiters bringing the food, or the waitress, and before eating it, they gotta take a picture of it, take a picture, and they gotta upload it to the internet, to Instagram. There are people in the gym working out in the gyms and taking pictures of them working out. It's really how buff they are. You get the point.
We get to learn about their pattern of life through Instagram. Where are they going on a regular basis that's not to their work and back home, because why is this important? In addition to learning about some of their interests, we can learn where we can accidentally bump into them and set up this conversation and develop a relationship with them if we want to. That's important.
We can learn a lot about these things through social media platforms. Then think about this: There's a lot of different things I can learn about a company, and I'm not going to spend hours on that, but it's a simple tidbit. Glassdoor. Glassdoor, most people are familiar with it, and that's the place you can go to learn about what it's like to work for a particular company.
People will comment current or past employees, whether they liked it. “This company was the greatest thing. They treat you well. Lots of opportunities,” or, “This place sucks. They run you through the mill here. The management is not transparent. Everybody thinks about themselves and this is terrible.”
That provides us sort of with a compass, a bit of a pulse of what's the morale within a company. Are people happy? If people are happy, they'll typically be loyal to their companies. If people are not happy they're much more susceptible to being recruited and working against their company or working for themselves, even if it's to the detriment of the company. “What do I have to give? The company's not really taking care of me; now it's my turn.”
We can learn a lot about these bits and pieces through this different information that we can gather to then develop a number of different types of approaches to an individual. I think when we talk about social engineering—and we had this conversation earlier—a lot of people use social engineering as defining sort of what we are talking about. It's sort of like social engineering is individual.
I like to use the term human hacking because, actually, in essence, it's the same as a little bit more visual. You are hacking into someone's mind and getting to know how that mind works and how we might be able to—and I'll use the term manipulate—that person's right to undertake the objectives that I want to accomplish.
Today I look at how human hacking or social engineering can be conducted through five different communication channels. We have email. People think of email as phishing. We have text messaging, which is the same thing because there are links to be clicked on that can be malicious, or there can be attachments even in that text message.
We've got the links that we shouldn't be clicking on. We’ve got the attachments that maybe we shouldn't be opening, and those can be delivered, whether it's an email or a text. I mean those can be these hundreds and hundreds and hundreds of emails that go out, or it can be spear phishing, meaning you're targeting one specific individual.
If I've gone through this assessment of an individual that maybe it takes me a few hours to do based on what's out there, I can conduct spear phishing and craft that one message, that one individual and have almost a 90% certainty that they're going to take the bait, no pun intended.
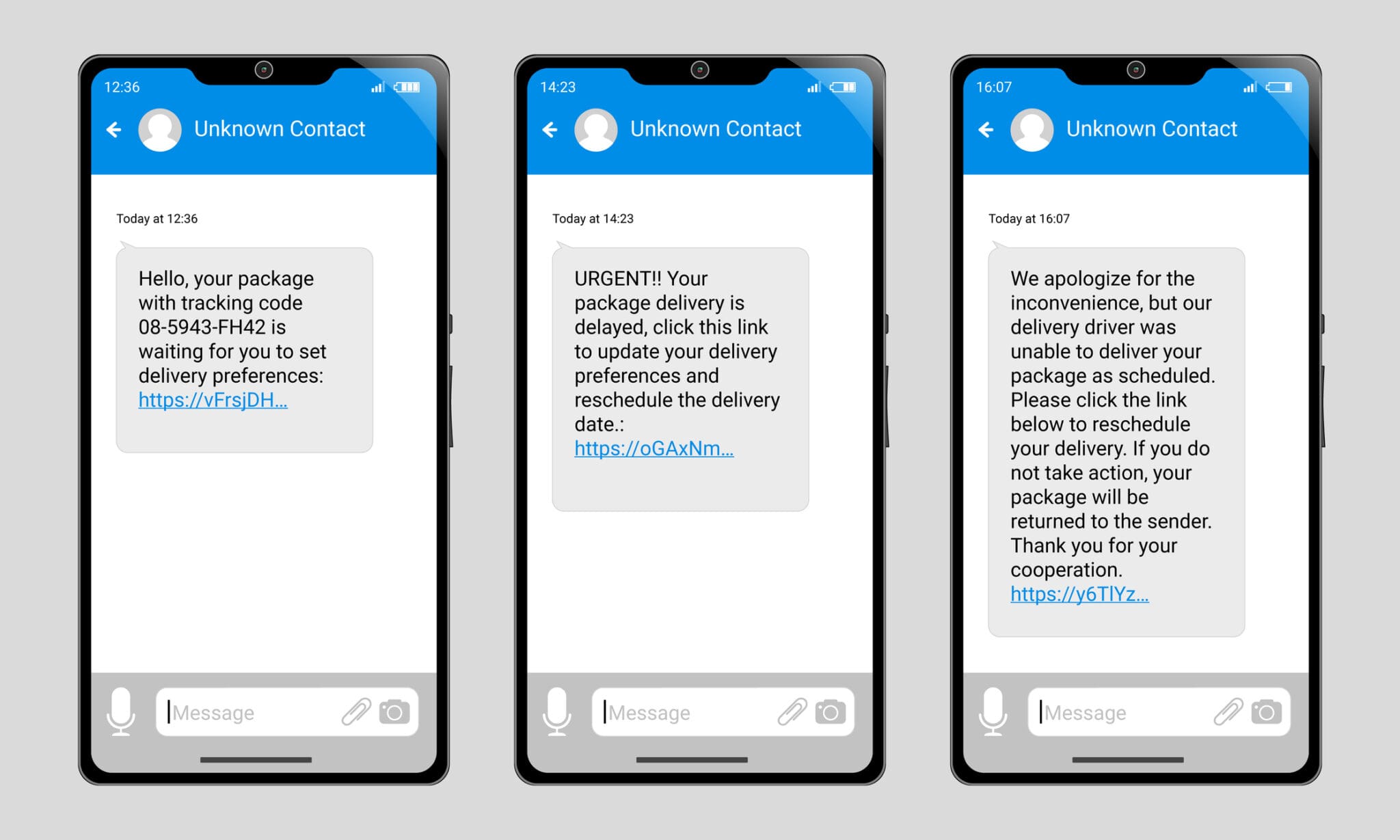
We’ve got phishing; we’ve got a smishing, which is text messaging. Then we've got a vishing, which is the telephone. [inaudible 00:29:05] is very, very powerful because as social engineers, human hackers can pretend to be whoever we want to be. When we connect with that person, it's amazing what we can do. We can be live monitoring how they're reacting to something that we're saying. We're using the pretext. We study them, and we use the pretext so we believe it's good to work with them.
We can use spoof-calling technology, which is available to anybody to make that look like a telephone call that's coming in from somebody that they might know, or an organization that they might trust, or maybe coming in from a vendor that they might do business with.
In addition to that, even with AI now, we can even clone the voice. That's a tremendous, powerful tool.
It's two different things that with that, you'd be in on the phone, might be to collect additional targeting information to be used for the attack, or it might be actually to conduct an attack, to getting somebody to disclose very sensitive information, or maybe change doing something online that compromises the IT network, or even, let's say, just issuing an access pass to somebody who's a threat actor who shouldn't have access to a particular part of the facility and all of a sudden, there's an access pass waiting for them when they arrive at the company.
Maybe it's issuing a wire transfer—this is big too—to someone who's not authorized, who has made it appear that this company's paying one of their vendors. In fact, they're not paying a vendor, and they're paying somebody else. Once that money is gone, and there's so many examples of that. The amount of money is even greater.
Then we have what still works very, very well today are these face-to-face attacks where social engineers will bump somebody and develop that personal relationship with them and get them to undertake something that's going to breach the network.
Let me give you, if I may, a very simple example. This is such a simple example. It has been used for years. I've used it. It's been used by intelligence services. It's been used by criminal groups, and it's continued to be used, and just think this through how easy this is.
Someone, a human hacker, will call a target and they will pretend to be an executive recruiter. This scenario happens a lot, even legitimate scenarios where somebody will call from a senior executive recruiter and they have a client. They're looking to fill that position for this client and they believe having looked at the resume of this individual and/or their LinkedIn profile that they would have been a strong possibility, good fit for this client.
They'll throw out a few things that kind of like gets the hook again like the title is higher with their current title. The salary is much larger and greater responsibility. Even if someone was not looking for a change in job, “What do I have to lose just to get together with this person for an interview over coffee or over lunch?”
A lot of people will accept that. “OK, yeah, we'll get together. Of course, I don't want to meet anybody in the office. I don't really want to tell anybody in my office that I'm going out for an interview, but get together.” This person already knows that they're going to have to share some information about what they do, what their company does, and what is normal.
The executive recruiter, the human hacker, will use this pretext and they will use normal interview questions. But in addition to that, they will use elicitation. They will get a lot of information and this could be easily in a 45-minute, hour, or two-hour meeting in an interview.
At the end of that, the person felt like a great meeting. They're looking forward to the results, and they may be told we might have to have a follow-on interview, depending on the school. Eventually, the human hacker gets back in touch with them. “Hey, let's get together again. I have some news.”
Well, the news is unfortunately, “That opportunity fell through, but I have another one. What do you think about this?” Once again, it looked very, very interesting. It's only a couple other people that are in the running for this and during that meeting, they're getting more information developing trust and this. Then they get together again, fell through.
Which is not unusual.
This time, this person, they're feeling really bad because their ego is deflated, didn't realize that this was going to be so difficult, and but then the human hacker says, “Hey, you told me during one of our first meetings that someday you wanted to be an independent consultant in the industry. I think I found a perfect opportunity for you. You can stay in your current position with your salary, with your benefits, but I found an individual who could be a great client for you. It's just as a matter of getting together with them once a month and sharing information about the industry, because they work in the industry and they really could benefit from your insight and so you could gain this experience so that later on, if you want to do this full time, you already got this experience. You can make some really good money on the side to be paid in cash or deposited to your account. You don't even have to declare it. What do you think? Is this something that could be of interest to you?”
It might even be where instead of introducing them to somebody else, it could happen, you introduce them to another individual as part of this scheme.
The human hacker said, “I'm actually doing some consulting for them as well, and what I can do is you can provide this information to me. We can continue to meet, and I'll pass that information on to them< and that's what they like. You kind of already trust us, and so we become the conduit between them and the ultimate client, let's say.”
They might believe the information is going to a company. They might believe it's coming to a US company. They might believe it might be a false flag. It's even going to a company that's from another country. It could be going to the government. It's hardly ever going to the CIA. They don't realize that it's going to the CIA. They believe it's going to another organization that's going to benefit from that information.
But at the same time, the individual’s benefiting. You're getting an experience. They're getting extra money that eventually changes their lifestyle. They become dependent upon this. This can go on for not just months, I've seen this go on for years and companies as well as organizations are hemorrhaging information and do not know it because it does not appear as a normal breach of the networks.
We gotta get away from the silo approach that all the threats are coming through and come through the IT network. That's where we're going to get breached. No, a lot of them are, but there's a lot of other ways that, if we want information for targeting your company, there's a lot of different ways that we can do it.
To me, that's a very simple approach, very simple and effective. When I try to talk to companies, I say, “Listen, you’ve got to understand that this approach is out there. It doesn't mean that you need to tell your employees not to interview. I mean, you don't want to create that, but you have to make them aware.”
If you're going to interview with another company or with an executive recruiter, you need to verify that they are legitimate before you go into that interview or before you go beyond that interview because this is a type of approach that's very effective. That's what we need to educate the organizations as well as the individuals.
I think I mentioned, I came out with a book when I first started my company because I started my company two months before Covid hit. What a great time, right? Everything was shut down, and it was like the worst time.
I always wanted to write a book, and that was the perfect time. I wrote my book and then I had to get it approved through the publication review board of the CIA. There's people that haven't done that and got into a lot of trouble, so I sent it in and fortunately almost the entire book was approved.
It came back, maybe 8% was redacted, and I had to go back a second time. It was approved and it's called Confessions of a CIA Spy: The Art of Human Hacking, and it's geared more for organizations, but individuals can learn a lot about it. Then I decided I wanted to come out with another book instead of just for companies, organizations. I want it to be geared more for the demographic that's most vulnerable to human hacking from scammers and fraudsters and that's our seniors. That's our elderly population.
It's amazing how victimized they are and, of course, there's the resources out there, but so few people are aware of it. It's a population that's vulnerable because, first of all, they tend to trust everybody right there. They were brought up in a time where you trust everybody until they prove to you that you shouldn't. They tended to have money. They have wealth compared to a 20-year-old. Who's going to be more interesting but target a 20-year-old or 65-year-old or 70-year-old, right? And they tend to be lonely. They like engagement. If someone approaches them, whether person, on phone, or via text, they like that. They welcome that opportunity to have that engagement, and they're not necessarily technologically savvy.
Some are, but a lot of times, one of the biggest scams are these technology scams. The tech scams. So people all of a sudden, they use a lot of different influence techniques, and a big one for them is fear.
“I've identified a really big problem. Your systems have been hacked,” or, “You haven't paid these taxes,” or, “The IRS is coming after you.” They use this fear to then get you to react without thinking things through, but then to react. Most of the time it's sending money. These individuals are so victimized. That's why I came out with my second book, Why Are You Messing With Me?
It focuses a lot on these different types of threats and scams that seniors fall prey to. These books are resources as well, so if anybody's interested in them, you can find them on Amazon under my name.
We'll make sure to link to those in the show notes so people can find them super easy. What are some of the ways that people can spot some of these techniques being used on them?
I used to say you gotta be so careful about what information you're putting out there, and you still do, but even if you're putting information, they say you want to have privacy settings.
But even if you're putting sensitive information on Facebook or another platform, and you have privacy settings, those platforms can still be hacked. That information can still be hacked.
Most of us—not all—I think I've been victim of maybe five or six or seven major data breaches, and so my PII—personal identifier information—is out there and almost all of your listeners, that information is out there.
I think we have to work now from more of a defensive stance. The information out there can be collected and we can be targeted. How do we prevent ourselves from falling victim to that targeting attack?
It's not when we reach out to somebody to try to get information or look at some product or service. It's going to be when someone contacts us. Whether it's through email, text messaging, voice phone call, or in person, that person is approaching us and they're giving us some kind of story. It could be legitimate or it might not be.
It's not that we’ve got to be paranoid regarding everything. What we need to have is a healthy sense of paranoia that we need to, if they are asking us of something, and if these individuals are fraudulent, if it's sensitive information they're asking for, or if they're asking us to maybe send them money.
If it's fraudulent, this can have dire consequences for me or my family or the company I work for, that's when we have to step back and not automatically undertake that action. We need to step back and verify that this is a legitimate request before trusting it.
A lot of people throughout this term trust and verify. No, even former President Reagan used that a lot. It's actually a Russian phrase. Trust and verify. In today's digital world, it’s too late. It is too late. You can't think that way. You have to think that we need to verify rather than trust.
If we do that, that simple three-word phrase, if we follow that, it'll save us from probably 95% of any attack attempts to try to successfully victimize or target us.

The verification is a little bit more complicated than it used to be, at least perceptually. It used to be that when the number on the caller ID was our bank, we would take that as a point of trust. But now we can't use those, some of the historic pointers for trust anymore or verification.
No, that's very true. Especially with AI. You have to go back and you have to kind of like do other types of Google searches to see this person show up and somewhere else in Google and not just on LinkedIn, because in LinkedIn, there's a billion profiles and there's about 15%, 150 million of those profiles are fake.
Don't take anything that looks like a legitimate LinkedIn profile. You still have to verify that. If you don't know that person, verify through some other searches about whether or not that person really exists, because it's the world. With AI, I like to say a lot of times we're living in a world with fraudsters now. They're using AI like steroids because they can use a lot with this.
A lot of people think, “Well, we're going to have AI tools to help us unmask AI fraud.” This is true. A lot of people, a lot of companies now have money and we're beginning to invest in some of these tools. But your common person—you and me—do we have money to buy these tools for ourselves? Especially do the seniors have money to buy these tools for themselves? No, they don't.
A lot of these things that are out there that people think are great, we hear about this cloning of the voice. You'll hear about ChatGPT, but a lot of these things that are legitimately offered by AI companies have guardrails. There's a certain amount of ethics and laws and hopefully those are increased.
You can't use ChatGPT, because I know a lot of your audience is probably familiar with searching and scraping the entire internet to collect all this information even though the technology is there.
They take the guardrails off. They can scrape the internet and collect all this information, which now instead of spending hours and hours and hours trying to research your profile online, and especially your social media platform, your profiles, I can just scrape all this up. That's not allowed, but you take off those guardrails and you can do it.
On the dark web, there's a subscription service called FraudGPT, which is just like GPT without the guardrails, and usually you can scrape the internet. You can use it to make perfect phishing emails or different types of things that a lot of these people that are attacking us, English is not their native tongue.
A lot of times, this is previously to AI, a lot of these scammers you would see the grammar is not quite there. It was going too thin. But now these things are really well-worded. You're really legitimate.
The technology is there to really use this against us and we have to be smarter. It's not only the AI tools that are going to help us, but we also have to be smarter and how we react to that incoming request that we do something. Verify then trust.
It used to be that you get an email from someone claiming to be the CEO of a Fortune 500 company, and they love your profile, and they want to get to know you, but they can't put two sentences together in English. It's like OK, the Fortune 500 CEO probably has better English skills than that. Those points of perception that we say, “Hey, something's wrong here,” those are going to start to go away on scams.
[inaudible 00:45:38] study you and they know kind of like what your motivations are and I get hit up, I think literally 15 times a day, whether it's emails or text messages or phone, phone calls that I know, not all of them I'm saying are fraudsters.
Some of them are just trying to make a living, but there's different things that they've studied you in advance and they're trying to get a hook in you and hoping that what they're going to offer you. Since I'm an author of two books right now and especially a self-published author, I get hit all the time by these individuals that claim that they can really help put that book out there and get it on the bestseller list. Then I just start doing Google searches on those names of those companies or individuals and you'll find other people that have been scammed by them and they'll put something on there on Google.
That's why it's so important that one of the first things you should do is do a Google search of that name of that company or individual and scam and fraud. If there's someone that's reported it, you'll pop up right away. You'll find that probably in 90% of the cases, you're going to see, oh man, it's an easy way to be able to identify something as you don't want to go down that rabbit hole.
Or it just doesn't exist.
Exactly. In my career, I impersonated a lot of different people, made a lot of things up, so I know how it's done and I know how you can fall victim to it. This is why my mission today really is trying to help people understand this and it's not getting better. It's getting worse because of technology. People are very complacent and companies need to train their personnel.
I think we're finally seeing more of that being talked about because before it was just technological solutions and some of these technology companies say, “Don't waste your time trying to train people. It's not effective.”
I think, “Gosh, we got to this point where you cannot have faith that you cannot train your people to be smarter.” I want to really get this point in because I get on a soapbox. I think the training paradigm in most companies is completely upside down because this is treated as compliance training once a year where you're going to watch these videos, these cheesy videos, and then you're multitasking. It's on demand. You watch the video. You come back and you take a test and as long as you get 70% or above, you pass. If you don't get 70%, well, you can take it again and again. Eventually, you're going to get your certificate. You turn that forward to your supervisor. Your supervisor collects those and turns those over to his or her supervisor. “We're 100% in compliance for another year.”
What have the employees learned? They've only taken this training—most of them—because they need to comply or they'll lose their job, but have they found it valuable? Do they really understand why this is important?
I think it should be sold to the personnel.
Not sold literally, but it should be perceived as a benefit for them. They can learn how to protect themselves and their family from human hacking, especially from fraudsters trying to steal their money or identity theft if they understand how it's valuable to them to see it as a benefit. It will naturally come back and they will use that in the workplace.
I think we need a total shift in how this training is conducted. Not just only how it's conducted, but by how it is perceived by the individuals who really can make it happen.
That's a great point, and I know many people who only do those things because they're obligated to do them, not because they're interested in learning how to protect themselves because it's never pitched as, “This is going to help you,” but it's always pitched as, “This is going to help the company.”
Yeah, so often. Another thing is what we need are more testimonials from an individual side as well as organizations. I can understand a lot of companies when they get hacked, there are times when they have to report it. We're not going to go into that, right? There's certain laws that they have to abide by, state or federal, whether it's a public company or not, where they might have to, by law, report the breach. If they don't have to report it by law, a lot of them are not going to want to report it because it can be seen as hurting their reputation and all these different things.
I understand that. Or maybe opening up to litigation and other things like that. A lot of companies won't report it.
A lot of other companies are not learning about how these hacks have taken place, because if they would hear it because of testimonials by some of these companies, it could really have a major impact. As well as individuals who are compromised, maybe who lost a lot of money, whether it's seniors, especially seniors, but younger people as well, 30s and 40s, they don't tend to provide testimonials either cause they're embarrassed.
These are not being reported. People don't have the benefit of learning. They'll never happen to me, but they hear it happen to someone just like them and you hear these stories that will also have a major impact.
I try to get testimonials. I like to put testimonials on my website, not necessarily—we don't have to identify the individual, but sharing this is what happened to an individual and walking them through. This is how it happened. These are unfortunately now.
Instead of having enough money to have a comfortable retirement, they're scratching by now getting a part-time job and they're worrying about being able to pay their bills every month. It's awful.
Yeah, it absolutely is awful. I appreciate the effort that you're putting forth in this space, and I'm excited that so many more people are kind of entering this, “Hey, I want to do something to help protect the public, to give people the tools that they need to protect themselves, protect their families.” I super appreciate you doing that.
If people want to find you online, where can they find you?
Yes, virtually. They can find me virtually. Probably the number one place, the easiest one would be on LinkedIn. If you have LinkedIn, look me up there. There's a lot of information. Don't worry, even if you want to connect with me, I'll definitely do my little due diligence, but it's not a problem.
I'm welcome to connect with individuals, and you can ask me questions and I'll respond, but also you can find me on my website at www.counterintelligence-institute.com. Those are the two easiest places to find me. I reside in Orlando, but I'd be happy if individuals are interested in me providing presentations to your organization or your company or association. I'm happy to do that, whether it's in person or virtually, so please reach out if you think I can share something that could be a benefit to you or your organization. I love to do this type of work.
Awesome. Peter, thank you so much for coming on the podcast today.
Thank you very much, Chris. I enjoyed it very much.


Leave a Reply