
When a recruiter contacts you, it’s essential to do your homework, verify their sources, and trust your instincts. If something seems too good to be true, it probably is. While it can be frustrating to be this skeptical, being cautious can protect you and your finances. Today’s guest is John Sidoti. John is the Senior Director of Information Technology at Social Current. He has over 30 years of experience as an IT generalist with wide and varied experience across all aspects of the IT spectrum.
“If it looks too good to be true, it probably is.” - John Sidoti Share on XShow Notes:

- [0:50] – John shares his background and discusses his extensive and varied career in IT.
- [3:32] – Even as a director, John keeps hands-on projects going to keep working in the field.
- [4:45] – John describes an experience of himself falling victim to a scam on LinkedIn.
- [7:56] – At some point in the process, John realized that something seemed off.
- [9:40] – After speaking with this scam company, he continued to receive copied and pasted messages from other “recruiters”.
- [12:21] – Although the copy and website look and sound very legitimate, there are some things we can look for that raise red flags.
- [14:13] – Many scammers create fake profiles that look very professional and well done. But take the extra step and research the company and individual.
- [15:57] – In the grand scheme of things, the people who have been victimized by these types of scams are vulnerable and desperate for employment.
- [18:22] – Anyone can purchase a domain name and pull together a website using a free or cheap template that all look very legitimate.
- [20:05] – Once you know the markers, you can see them coming.
- [21:07] – Look at the domain names and how long they have been registered.
- [22:30] – Don’t assume it is just an email world. If a company does not have a legitimate phone number, it is a red flag.
- [24:02] – Another red flag is when a recruiter has been working with just one single company in their career.
- [26:45] – Recruiters should not be asking for personal information. The company will do that, not a recruiter.
- [29:43] – It’s okay to be a little cynical about this in order to protect yourself.
- [31:34] – There are other places that need to be looked at closer as well, specifically Facebook Marketplace.
- [34:16] – When you look closely at sponsored posts that seem too good to be true, you’ll notice that they are all from bots.
Thanks for joining us on Easy Prey. Be sure to subscribe to our podcast on iTunes and leave a nice review.
Links and Resources:
- Podcast Web Page
- Facebook Page
- whatismyipaddress.com
- Easy Prey on Instagram
- Easy Prey on Twitter
- Easy Prey on LinkedIn
- Easy Prey on YouTube
- Easy Prey on Pinterest
Transcript:
Jeff, thank you so much for coming on the Easy Prey Podcast today.
Chris, I’m glad to be here. Thanks for the invitation.
I’m excited for this conversation. Can you give the audience and myself a little background about who you are and what you do?
I’m a partner at ObscureIQ, and I’m a data privacy researcher. One of my specialties is understanding the data broker ecosystem and really all the commercial surveillance that’s happening to all of us now.
How did you get into the field?
That’s maybe a little bit of a long answer, but I was actually in marketing and technology for a long, long time myself, so I understand why people want to track. Maybe 15 years ago, I got involved with a search engine company and started understanding how younger teens and young adults were sending questions into a search engine. That got me really interested in digital identity and digital privacy. I started studying that.
One of the things that I ran across way back, maybe in 2012, was an article by Kashmir Hill about data brokers. These data brokers in this article she wrote was they were selling lists of car accident victims, of men with impotence problems, and of women who had been raped. This was just really invasive information, and I was like, “They’re actually just selling this?” It was crazy to me.
That was actually when the first time the data brokers of personal information came into my purview. While I was actually working for the search engine, we were building out the back end of some knowledge graphs and other data science-y things. I was actually working with data brokers of another sort, not for personal information, but buying big chunks of data. I was interested in understanding that space already.

As that progressed, I studied that more and more, got into the CAN-SPAM laws, got into understanding COPPA—the Children’s Online Protection Act)—and it just evolved into an interest of mine. When that finally failed, that operation that I was in, I got more into data privacy. Instead of getting into compliance like most privacy professionals, I wanted to get in at the intersection of data privacy and data science.
What I really do is build data sets about data privacy to try to understand it from that angle. The biggest data set that I’ve built is one about commercial surveillance or trying to understand the data broker ecosystem. I have built the largest data broker database that we call the Codex, and it has over 8,500 organizations that are collecting consumer profiles about you and me.
That’s a lot of companies.
It is, isn’t it?
Let’s talk in context. There was a large data breach in 2024, I think it was early 2024, NPD if get that right. Would they be considered a data broker?
They would. Pretty classically a data broker. I actually forgot what exactly they were doing. They were essentially selling not credit reports.
I think they’re an identity verification service.
Exactly.
Which means they have to know a lot about you.
Right, and they were essentially just buying lots of data from different organizations and putting that all together. They were sort of like a background reporting company. There are all kinds of those out there, mom-and-pop shops. This one was a relatively big one, but there are hundreds of those organizations out there.
It’s really hard to get a handle on these organizations because literally nobody’s tracking them. There are a couple of state laws out now. California and Vermont were the first states that started asking these organizations to register, but there are only, I don’t know, 600, 700, maybe 800 organizations that are registered as data brokers at this point.
Part of that is because the legal definition of data brokers is relatively narrow. You have to be a third-party data broker. If you have a direct relationship with the consumer, then you’re not a data broker. You have to have a certain amount of your revenue and you have to do certain other things. There are little loopholes that these organizations can hop through to not be labeled a data broker.
We have a larger remit, and that’s why sometimes I call it commercial surveillance instead of data broker. If you collect consumer information, I put you into my database, whether you’re legally a data broker or not.

Got you. From the least invasive to the most invasive, what kind of data do these data brokers have about people?
It can really be anything. It might be healthcare data, it might be your basic information that they can grab from voter records or Department of Motor Vehicle records, both of which get sold, by the way. They also sometimes grab it from court records or real estate transaction records. They get it from credit card transactions. They get it from medical pharmacy transactions. They get it from your viewing habits on the web.
Virtually anything that you do that’s digital dust, they’ll hoover up and vacuum up. If they’re not getting it directly, they’ll buy it from somebody who does.
Would that include cell phone location data?
Absolutely.
That’s scary.
That’s some of the worst stuff actually because you cannot only use that stuff directly to have a lot of intel about people, but you can infer a lot of information about people from that information indirectly.
What things can you infer about people based on their location data?
Let’s say you wake up in the morning. You drive to the grocery store, then you drive to the liquor store, and then you drive to another location, another location.
All these different places that you go give you, first of all, a pattern of life that you could build a story about somebody, but then each location that you hit—OK, maybe you’re buying liquor, maybe you’re buying pot, maybe you’re driving to a school, maybe you’re driving to different locations—this is all telling me about you. All those data pieces I can put together tell me what kind of person you are in ways that the other data points by themselves might not. I can develop an interesting story about you that might be true or might be completely false.
All those data pieces I can put together tell me what kind of person you are in ways that the other data points by themselves might not. I can develop an interesting story about you that might be true or might be completely false.… Share on XA story that looks to be true because, “Hey, we have all this evidence that points towards the story that we’re making up.”
Exactly. We have a pretty interesting example that we give in seminars, where we have this woman who has a son and she’s going around to different locations. It looks like maybe she’s like a woman who gets drunk every night and doesn’t take care of her kid very well, and has a habit of going by the weed dispensary all the time.
But an alternative viewpoint might be that she actually has a son and she takes care of him really well, and she’s actually going to the weed dispensary to get it for her father who is actually in a home or someplace. She’s actually taking that for him and visiting him once a week and making sure he’s OK. So she’s actually a wonderful woman doing everything she should be doing, but people can infer the wrong thing from the data points based upon their analysis.
She’s picking up a friend of hers that works at the bar, not going there herself.
Right, or maybe she’s actually working there as a second job. She’s not actually drinking every night; she’s working. The data points can be interpreted in multiple different ways.
How accurate is the location data that’s available through brokers? Is it just city-level or 1000 feet, 100 feet, 10 feet, one foot?
It can be very, very accurate. It can be very precise geolocation. But you ask a really interesting question because it’s not always clear. When an app gets your location information—the apps are generally the ones that sell to the data broker—the app is not always clear what level of specificity or granularity that location data is getting, because it could be coming from the operating system. They’re just grabbing location services.
It could be very precise geo data, or it could be more cell tower inference data, or it could be very precise Bluetooth data. You don’t really know all the time. And it could be changing back and forth. It could be precise, precise, precise, then all of a sudden you’re half a mile away and that’s not actually you. Oftentimes, when you look at this geolocation data some of the data points don’t make sense because they actually are wrong.

And it’s the same way with IP geolocation data. It could be precise down to exactly where the side of the house that your router is sitting at or when you’re sitting in your home office, and it could be hundreds of miles off. You just don’t know which record is exact and which record is totally off.
Absolutely.
As consumers or individuals, what the heck can we do about all this data of ours that’s floating around out there?
We usually think of it as a two-step process. One is you should really delete your digital footprint. We and other services can help with that. There are consumer-level services that can help you with a little bit of that data. We have more professional services that are much more expensive that can delete it much more effectively.
But in addition to deleting your footprint, you actually have to stop leaking the data. Frankly, you have to change your behavior. You have to get rid of apps that are tracking you. You have to stop using certain types of software.… Share on XBut in addition to deleting your footprint, you actually have to stop leaking the data. Frankly, you have to change your behavior. You have to get rid of apps that are tracking you. You have to stop using certain types of software. You have to change some of your behavior so that ad tech can’t track you as well. Part of that is just understanding how all this stuff works.
It’s not necessarily that the government is out there tracking you, unless you’re a certain type of person who you know they’re going after. There are people that they want to track, but most of this they don’t care about. But the ad tech industry is tracking us by default. They do that in certain ways, and we have to take measures if we don’t want to be tracked because all that technology is just doing it by default—Google and Apple—frankly every other technology that we use on a daily basis.
And to me—I’ve always known this is necessarily an argument—it’s a double-edged sword in a sense that good ad tech means relevant ads and businesses paying less money for their ad spend because they’re targeting the right consumers. But on the consumer side, it’s like, “Well, now there are a lot of people who know an awful lot about me. Maybe I don’t want this.” It’s an interesting push and pull on the value of ad tech.
I would agree.
Competing interests is maybe a better definition.
Absolutely. There is some value in targeted advertising, no doubt. I think that the whole ad tech infrastructure is out of whack, and there’s much less value going to the advertiser than the overhead that it’s presenting at this point in time.
There are lots of ad fraud, there are lots of things that advertisers are paying for that they’re not actually getting. For the consumer, I think that there’s a lot of value that they’re not getting and there’s a lot of disadvantage that they don’t understand that comes along with it. While I can target you with an ad, it’s not always to your benefit.
Correct.
They don’t understand that part. Yes, I might be giving you a 10% discount, but I also might be giving you a 10% surcharge. They have to understand that part of it as well, that it could be targeting that’s not making you happy.
But you’re right. In the best of all possible worlds, it could be a good thing. I just don’t know that we’re living in that best of all possible worlds.
It’s definitely double-edged at best. Maybe triple-edged is a little bit more. As consumers, how are we seeing this data being exploited, either legally or illegally?
Well, I guess in lots of ways. You turn on the news and every single day there are one or two or five data breaches. All these companies are collecting this information about us, but they’re not securing it. Some of them try and fail because frankly, trying to secure data in a database is hard. We just don’t understand how to do it very well at this point.
If you’re securing data in a data structure and you’re not encrypting it down to the field level, it is very hard to keep that data safe, and companies just aren’t doing that. -Jeff Jockisch Share on XIf you’re securing data in a data structure and you’re not encrypting it down to the field level, it is very hard to keep that data safe, and companies just aren’t doing that. There’s that.
But then there are a lot of companies that aren’t taking those measures. They aren’t being safe enough with our information. Some of those companies are third-parties that don’t really care about us and our data. They’re just monetizing our data. We’re not even part of the equation for them. They’re just grabbing our data and selling it.
The third-party data brokers are maybe the worst offenders there. There are thousands of those companies that they’re just out to make a buck by analyzing our information and selling it onto another company. The first-party companies have much more invested in not having a data breach, but even they’re still having problems.
AT&T, Verizon, T-Mobile, all the major cell phone carriers have had a data breach probably within the last year that we know about, let alone the ones they don’t know about.
Right, and part of that problem is not actually them directly securing the data. The problem is infrastructure. They give the data to their friends, their providers, their suppliers because they’ve got to process that data, because they can’t do everything themselves.
You give the data to AT&T and they give it to these 10 other people downstream, and they give it to five other people each downstream. Pretty soon, 500 organizations have your data, and one of them is going to get breached.
How are these data breaches being used illegally?
That’s the bad thing. Our data’s all ending up on the dark web. It’s becoming easier and easier for criminals to monetize that.
If you think about it, what are our data brokers really doing? They’re building consumer profiles on us. The bad guys are doing the same thing. They’re not just taking a couple of pieces of data about us and saying, “OK, what can I do with that?” They’re actually aggregating multiple different data breaches together and building larger and larger consumer profiles.
Once they’ve got a large consumer profile, what can they do with that? Well, they can start doing synthetic identities. Or pretending to be us and going out getting loans, or buying property, or trying to take over our bank accounts.
We talked a little bit earlier about this sextortion scam that’s going around. We know there are now millions of emails that are going out to people claiming that they know that you’ve been surfing porn and saying that they’re going to release all that information to your friends and family and employers if you don’t pay them $2000 in Bitcoin.
It says, “Hey, Chris Parker. Here’s your address. Here’s all your information. Here’s a picture of your house. We’re coming to get you if you don’t pay us $2000 in 48 hours.” It’s this fear factor that gets some small percentage of people to respond, but they don’t know who the hell you are. It’s just information they got from a data breach. They don’t have any information on you. But they know that some percentage of people are going to get freaked out and send them money.

And the better profile they have of you, the more convincing those threats can be because now they can say, “Here’s your phone number, here’s your address, here are the names of your family members.” It’s not just, “I’m going to tell your friends and family. I’m going to tell your wife whose name is this, and your kids and your parents. We’re going to send it to your neighbors at this address and this address. Your community’s going to know.”
And they can get that information from different data brokers. If you go on the web, most people, if you haven’t deleted your digital footprint, you can go to beenverified.com, look your name up, and you can see a list of people that are connected to you. You can see a bunch of addresses that are connected to you, phone numbers that are connected to you.
If you have access to the right tools, you can get better information. You can probably see a list of your actual relatives, who they are. There are open source intelligence tools that can tell you a lot about most Americans. There are PI tools you can get if you have a private investigator license that’ll give you a 50-100–page report on most Americans. That should be scary to you.
How effective are both the consumer data removal services and the things that you guys do?
Well, the consumer services are decent. I don’t want to knock them. If you get them, it will get rid of the surface-level stuff so that if you search for your name, generally there will be a lot less stuff that comes up. It’ll de-index a lot of that information that’s easy to get to, so there’s some value in that. But it’s not going to get rid of everything for a determined attacker who wants to try to find you. That stuff’s still going to be available. They’ll still be able to get to you.
Is there a way to get rid of that stuff? Because if it’s public records, aren’t you stuck?
Well, it depends. You can get rid of more and more of that if you know how to do it, if you know how to go about changing public records, for instance, if you know how to go after these data brokers to make them delete more of your physical records, because they don’t have to delete your whole record.
Essentially, the privacy laws that most consumer services use are just going to get them to de-index stuff; it’s not going to get them to delete the public record because they’re not under any obligation legally to do so, first of all. Because if it’s public information, they don’t have any legal obligation to delete the information.
Because it’s nothing that’s not publicly known.
Right. Now there are ways. If you’re actually under threat, you can potentially force them to delete that information under legal threat because if something were to happen to you and they didn’t delete the record, then you could sue their ass. But will they respond or not? That depends upon whether they want to or not to some extent.
And how ethical they’re choosing to be. I assume there are probably a number of large data brokers that are very ethical, that when they receive removal requests, will process them and not disseminate that information, that will delete it from their databases. But I’m sure there are even more that all those things just go into a black hole.
It’s a spectrum. You’re right.
We’re painting a bleak future here, aren’t we?
Well, it’s not pretty. There are things that are happening. There are more privacy laws that are getting passed, but we could certainly use everyone’s help in getting better laws passed. There are lots of people that are saying, “Hey, we have no data privacy. It’s not even worth fighting anymore.” That’s not true at all. We’re actually making significant progress now.
The problem is that the data brokers are massively powerful. It’s a $400 billion industry at this point, probably larger than that because it’s dark. So we need to fight that, and it’s a lot of money against us. These data brokers are large and powerful, and they don’t want to give this up.
But 80% of consumers are on the side of this issue. They don’t want this going on. It’s an issue that both sides—whatever political spectrum you’re on—does not want this. You’ve got a lot of politicians that want to help. They’re trying to fight back. We’re trying to get some good policy passed and we’re making progress.
There are things like the California Delete Act that are going to help consumers delete their information. That has actually already passed. It doesn’t go into effect, I think, for another 14 months or something like that. But at that point, Californians will be able to, with one stroke, delete their information from 500 or 600 or 700 data brokers, and that’s going to be a massive win.
But we need to do that nationwide and for more people. Frankly, we need to widen the scope of that. It should be more than just those data brokers that register and are within that limited scope.
In the meantime, before these things go into play—we talked a little about trying to reduce your digital footprint—what specifically can we do on two levels, both get data out and prevent data from going in? What does our mindset need to be?
I think to prevent things from going in, I’ve got two pieces of advice. One is to check out some resources that we have on our website on ObscureIQ. We’ve got all kinds of different things that can help you delete your digital footprint.
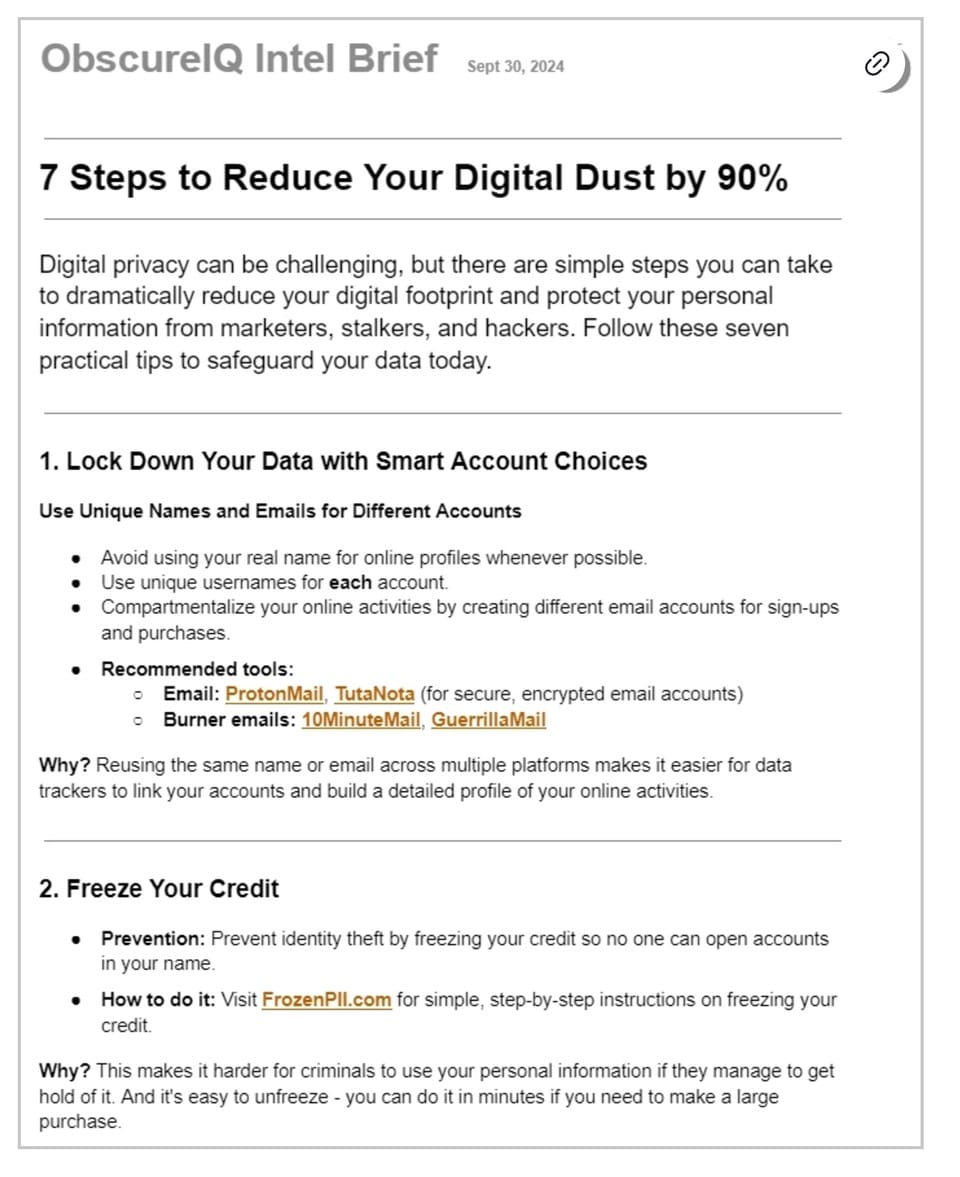
I’ve got another one that’s going up that we just produced called Seven Steps to Reduce Your Digital Dust By 90%. It’s essentially just seven relatively easy steps. Straightforward steps, maybe not easy, that will really delete how much data you’re leaking.
Then we’ve also got a new newsletter that I put out called Tactical Privacy Wire. That will give you new issues on a weekly basis and give you specific advice on how to do things, like how to not leak your voter record information. Or if you’ve been in previous states, you may have open voter information sitting out there.
We’ll do new things, like I’m getting ready to do a new one on how you can create a secure sock puppet if you want to go on social media and not give everybody your information when you’re giving them your viewpoints on issues.
That would never happen of controversial viewpoints in a political system like we’re currently at.
Oh, it’s terrible. We just did a seminar on digital citizenship and how it’s hard to go out there and state your opinions without getting doxed nowadays, because somebody’s going to take offense to what you’re saying.
Just don’t say anything ever online.
It’s pretty hard, yeah.
I’ll get the links for those resources from you, and we’ll make sure to include those in the show notes. One of the other questions that I ask my guests that are in the cybersecurity counter-scam, counter-fraud space is, have you ever been a victim of scam, fraud, or cybersecurity incidents?
I’m asking you that question now, because I want the listeners who, “Hey, this has happened to me and I don’t want to talk about it. I don’t want to let anyone know.” But if you and I can’t get it right 100% of the time, they shouldn’t feel ashamed, discouraged, or embarrassed if they can’t get it right 100% of the time. I’m asking the question in a very leading way because I know the answer to it.
Well, they didn’t get me, but they almost got me. A couple of years back, I was expecting a phone call because I did something stupid. I got a phone call and I thought it was the guy that I was supposed to get the phone call from, and it was somebody else. I let bad guys into my computer. I didn’t realize who it was, and I actually gave him access to shit, and it was stupid.
Then I didn’t realize what was going on until they started asking me for money. I’m like, “Holy shit. What the heck did I do?” It was bad, bad guys. I had to throw the damn computer away. I was so concerned.
Anybody can get scammed by these guys. They take advantage of you by getting you in the right circumstance, in the wrong frame of mind. -Jeff Jockisch Share on XAnybody can get scammed by these guys. They take advantage of you by getting you in the right circumstance, in the wrong frame of mind. Think that there’s somebody else. You think it’s a situation that it’s not a situation that it is. That is clear social engineering.
Now, I don’t know how they managed to figure out that I was expecting a call from someone else. Maybe it was just accidental. They just had the right timing. But they did it. Holy crap. They almost got me.
I know that feeling. On one of my phone numbers, it’s gotten to the point where the scam calls have gotten so incredibly pervasive that I have turned on the feature on the phone that basically says, if the phone number’s not in my address book, it just goes straight to voicemail. It doesn’t ring, it doesn’t bother me.
But occasionally I’m expecting a phone call from someone that I don’t know what phone number they’re going to call from, so I’ve got to turn off that feature because otherwise….And all of a sudden the scam calls come in. I’m like, “OK, I’ve got to pick up the phone because it might be this one call that I need.”
“Oh, hey. Your power’s about to be shut off.” “Hey there’s a bug on your computer.” “Hey, there’s….” Oh my gosh; this is incessant. I can’t imagine, like in your situation, you were expecting a phone call in a particular situation, so you took the call because it was exactly what you were expecting, so why wouldn’t it be the right person?
When the scams have gotten so pervasive that there are a million calls a day are just going to get someone in that right spot, it wasn’t your fault. You didn’t do anything wrong.
Well, I still shouldn’t have given them access to my computer. I feel like a total noob for doing that. I was like, “Why the hell would I do that?”
Because it seemed reasonable at the moment.
It seemed reasonable.
Yeah, it’s absolutely not.
But that’s what victims always think. They always think that seems reasonable at the moment.
Very seldom is it, while we see those emails of, “Hey, I’m a Nigerian prince, and I want to give you $10 million.” We joke about those. The scams have gotten way more sophisticated nowadays than they ever were in the past. I just see it getting worse with these massive data breaches and, “Hey, let’s just merge all these data breaches into one massive database.”
Now, I just pick a phone number and I now know the name of their dog and where they grew up. Now I can pretend to be, “Hey, I lived next to you when you lived on this street as a kid, and I want to reconnect.”

Well, think about it too. It’s not just that some scammer out there has to be that smart. They can use an AI to do that, and they can use an AI to do it a thousand times, not just three times or five times or 20 times.
What I hear you saying is find a rock and crawl under it.
It’s going to get really bad. I think it’s going to get really, really bad.
OK, so all my stuff has been breached and it’s out there. Every legal, legitimate data broker who doesn't even want to be cooperative, let’s say I can get everybody to delete my data. It doesn’t delete the stuff that’s already been breached.
No. You have to start changing things up.
We have to teach our kids really good behavior, so that they don’t have stuff to be breached or limited stuff to be breached. Ugh, that’s awful.
If people want to find you, where can they find you, and how can they connect with you?
I’m very prominent on LinkedIn. Or you can find me at obscureiq.com.
Awesome. Jeff, thank you so much for coming on the podcast today. I super appreciate your time.
Absolutely. Take care, Chris. Wonderful talking to you.


Leave a Reply